Beth Musumeci
Wilmington
An average of 1,258 cybersecurity attacks occur weekly across global organizations. Enterprises invest over 11% of their annual IT budget in cybersecurity to safeguard customer and organizational assets against potential breaches. The ramifications of a cyber breach have proven to stifle an organization's business operations. Many organizations maintain a robust incident response ("IR") playbook. Yet, a tremendous strain can be placed on organizations to resume normal operations that affects long-term financial performance, contractual obligations, and other legal and regulatory considerations.
Cybersecurity is a fundamental enabler in achieving corporate strategic objectives and is at the forefront of investors’ concerns with the persistence of reported cyber-attacks. The Securities and Exchange Commission ("SEC") adopted new cybersecurity disclosure rules on July 26, 2023 that standardized how registrants report on their cybersecurity programs and the timing and content of disclosures regarding material breaches.
Watch our webinar with DLA Piper and SEC staff where we discuss insights on what the new rules mean for companies, boards, and investors.
These new rules call for increased transparency of registrants' cybersecurity programs. Ahead of their final adoption, registrants and other stakeholders raised concerns associated with divulging sensitive cyber program details that could be exploited by malicious actors. Ultimately, the SEC determined that such information may be material to investors and included requirements for registrants to disclose information on their cyber risk management practices in the final rules adopted.
With the spotlight on cybersecurity, senior executives and cybersecurity leadership have a unique opportunity to enhance the enterprise risk management program by integrating the organization’s cybersecurity processes. To address the Risk Management and Strategy requirement (Regulation S-K Item 106(b)), registrants must outline how the cyber processes are integrated within the global risk management program, specify the third-party advisors that support the cyber program, and describe the third-party provider monitoring practices. Similarly, the Governance requirement (Regulation S-K Item 106(c)) mandates that organizations describe the management position(s) responsible for cyber risk management, highlighting their relevant expertise, and the cyber risk and incident reporting practices to the board of directors or subcommittee(s). These requirements go into effect for fiscal years ending on or after December 15, 2023, and the disclosures must be made in issuers’ Forms 10-K and Forms 20-F.
The risk management and strategy, and governance requirements may not require sweeping changes in how some organizations operate their global cybersecurity program. However, the Material Cybersecurity Incidents requirement (Form 8-K Item 1.05) will require registrants to evaluate and evolve their IR playbook and processes.

Figure 1: SEC Cybersecurity Disclosure Rules
In the event of a cybersecurity incident, an organization's ability to identify real-time cyber threats and enact prompt containment activities is predicated on an expansive IR plan. It is common for organizations to have established crisis communications practices to notify affected customers and regulators in a timely fashion. While an IR plan is foundational to the Material Cybersecurity Incidents requirement, there is an important nuance around the triggering event requiring disclosure of a cyber breach: registrants have just four business days following the determination that an incident is material to publicly disclose the event via Form 8-K. Specifically, registrants must provide details of the breach, including the nature, scope and timing of the incident, and address the anticipated material impact on their business operations and financial condition. These new rules will force organizations to balance the disclosure of the material aspects of the breach as required by the new SEC rules and not reveal specific technical details that may be leveraged by cybercriminals.
In anticipation of implementing compliance programs to align with the new regulations effective in December 2023, registrants must institute a scalable cyber materiality framework encompassing both quantitative and qualitative factors. Figure 2 illustrates a potential cybersecurity materiality framework, which captures common risk vectors frequently compromised during an identified cyber breach within an organization. Organizations must establish the core set of risk vectors that will be used to determine whether a breach is material in nature. Senior executives and cybersecurity leadership should jointly agree upon this framework, emphasizing the contextualized quantitative (e.g., lost revenue to system downtime) and qualitative (e.g., impact on employee morale) elements that factor into the total mix of information necessary to make a materiality determination. The objective of the cyber materiality framework is to guide relevant stakeholders to take a holistic view of the incident and evaluate the quantitative and qualitative impacts to determine if a material event has occurred within the enterprise.
While the SEC has not issued specific guidelines or framework companies can use to assess the materiality of a cyber incident, analogous guidance resides in the SEC's Staff Accounting Bulletin No. 99 ("SAB 99"). SAB 99 has long been the benchmark guidance companies and auditors use to determine whether accounting errors have caused previously issued financial statements to be materially misstated. We expect that SEC staff will require a similar rigorous evaluation of quantitative and qualitative factors to support decisions to (and more importantly not to) disclose cybersecurity incidents under the new rules. Our team adopted these principles in working with clients, see the illustrative cybersecurity materiality framework below.
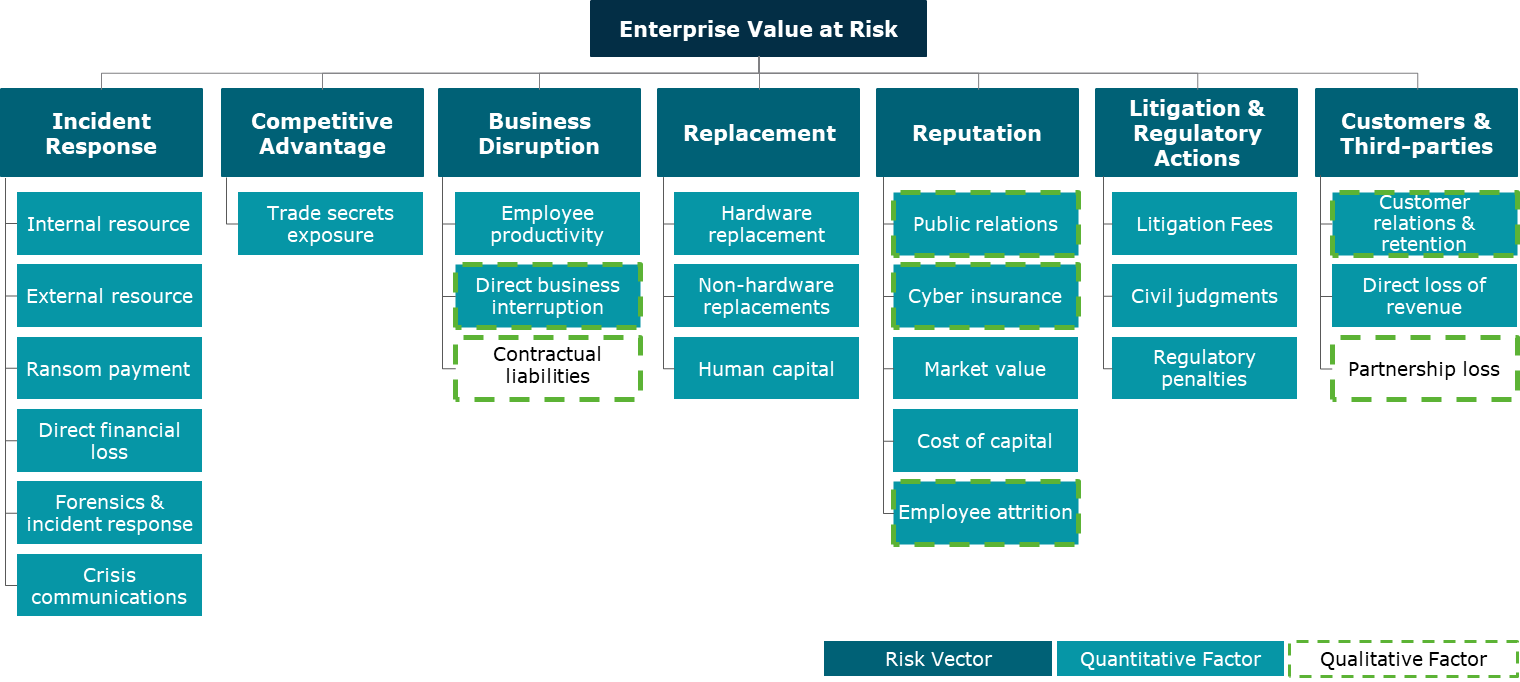
Figure 2: Illustrative Cybersecurity Materiality Framework
Many experts also expect SAB 99 to provide key guidance on how companies can evaluate the materiality of cyber incidents:
“I anticipate that the SEC will expect a SAB 99-type analysis, where both quantitative and qualitative factors are carefully assessed through a repeatable framework, by companies making an 8-K disclosure decision. But a SAB 99 analysis is only as effective as the inputs subject to the analysis. Cybersecurity professionals should be escalating, to a disclosure committee or a cybersecurity disclosure sub-committee, potentially material cybersecurity incidents pursuant to a reasonably designed and repeatable incident response plan. I believe that it’s now incumbent upon public companies to be assessing their disclosure controls and procedures through this lens.”
Eric Forni, Partner at DLA Piper focused on SEC Regulatory & Enforcement and a former SEC Enforcement Attorney
As companies continue their preparation towards compliance, they should keep in mind that materiality frameworks should not be viewed as a one-size-fits-all but rather as acceleration tools to enable them to have a standardized and repeatable process for evaluating cyber incidents. This is a process that will require input from a multitude of stakeholders and expert counsel. We expect that companies will need to customize adopted materiality frameworks to the uniqueness of their organizations and the facts and circumstances around each event.
It remains to be seen how the SEC will enforce these new requirements, but they put these rules in place for a reason. There is no reason to believe the Enforcement Division will shy away from enforcing them. Companies must be flexible and ready to evolve their cybersecurity materiality frameworks and disclosure protocols to best position themselves in light of inevitable enforcement investigations.